Overview
A data privacy framework is essential for organizations to manage and protect personal data effectively. It outlines practices and principles to ensure that personal data is processed lawfully, transparently, and securely. With the rise in data breaches and privacy concerns, implementing a robust data privacy framework is crucial for maintaining trust and compliance in any data-driven business.
Implementing a data privacy framework offers benefits beyond regulatory compliance. It enhances an organization's reputation by demonstrating a commitment to protecting the privacy of all stakeholders, including customers, employees, and other individuals. By fostering a culture of privacy, organizations can build stronger, trust-based relationships with their customers, employees, and partners.
A data privacy framework serves as a structured guideline for organizations to manage and protect personal data effectively. It outlines the practices and principles that ensure personal data is processed lawfully, transparently, and securely. As data breaches and privacy concerns continue to rise, implementing a robust data privacy framework is required for maintaining trust and compliance in any data-driven business.
The core principles of a data privacy framework revolve around data minimization, purpose limitation, and data accuracy. These principles are designed to ensure that personal data is collected only for specified, explicit, and legitimate purposes. Moreover, they stipulate that the data collected should be limited to what is necessary in relation to the purposes for which it is processed, ensuring that personal information is kept accurate and up to date.
The benefits of implementing a data privacy framework extend beyond regulatory compliance. It can significantly enhance an organization's reputation by demonstrating a commitment to protecting privacy of all stakeholders, including customers, employees, and other individuals who may interact with the company. Additionally, a well-structured framework can lead to better data management, reducing the risk associated with data breaches and the associated financial and reputational damages. By fostering a culture of privacy, organizations can build stronger, trust-based relationships with their customers, employees, and partners.
Components of a data privacy framework
Effective data governance and management are foundational components of a data privacy framework. This involves establishing clear policies and procedures for how data is collected, stored, accessed, and disposed of. Data governance ensures that data is handled in a compliant manner and that ethical considerations are integrated into data processing activities. By implementing a governance framework, organizations can ensure accountability and transparency in their data practices, which is essential for building trust with stakeholders and adhering to privacy laws.
Data classification and protection are also key elements of a data privacy framework. Classification involves categorizing data based on its sensitivity and the level of protection it requires. This process is necessary for identifying personal and sensitive data that may be subject to specific regulatory requirements. Once classified, appropriate protection measures, such as encryption, access controls, and data anonymization, can be applied to safeguard personal information against unauthorized access and breaches.
Reviewing data breach response and incident management processes is another key component of a data privacy framework. Organizations must have a well-defined plan for responding to data breaches, including procedures for notification, investigation, and remediation. This includes identifying the roles and responsibilities of team members during an incident, establishing communication protocols, and ensuring compliance with legal and regulatory reporting requirements. A robust incident management process not only helps to mitigate the impact of data breaches but also demonstrates an organization's commitment to protecting personal data and managing privacy risks effectively.
Implementing a data privacy framework
Identifying and assessing privacy risks is a first step in implementing a data privacy framework. This process also involves conducting privacy impact assessments to evaluate how personal data is collected, stored, used, and shared within an organization. By understanding the flow of data and identifying potential privacy risks, organizations can implement targeted measures to mitigate these risks. Privacy risk management is an ongoing process that requires regular review and adjustment of privacy controls in response to evolving threats and regulatory changes. Effective risk management is essential for maintaining compliance with data privacy laws and protecting personal information from unauthorized access and misuse.
Developing data privacy policies and procedures is essential for operationalizing a data privacy framework. These policies should clearly define how personal data is to be handled and protected, reflecting the organization's commitment to privacy. Procedures, on the other hand, provide detailed instructions for employees on implementing these policies in their day-to-day activities. Together, policies and procedures form the backbone of a privacy program, ensuring that all employees understand their roles and responsibilities in protecting personal data. Additionally, these documents may serve as a reference point for compliance with data privacy regulations and can be crucial in demonstrating accountability to regulators and stakeholders.
Implementing training and awareness programs for employees is another key aspect of a data privacy framework. These programs are designed to educate employees about the importance of data privacy, the organization's privacy policies, and their specific responsibilities in protecting personal data. Training should be tailored to the roles and access levels of different employees and updated regularly to reflect changes in privacy laws and organizational practices. Awareness programs can also include regular communications, updates, and reminders about privacy best practices. By fostering a culture of privacy awareness, organizations can reduce the risk of data breaches caused by human error and ensure that privacy considerations are integrated into all aspects of their operations.
Data privacy framework FAQs
What are some generally accepted data privacy principles?
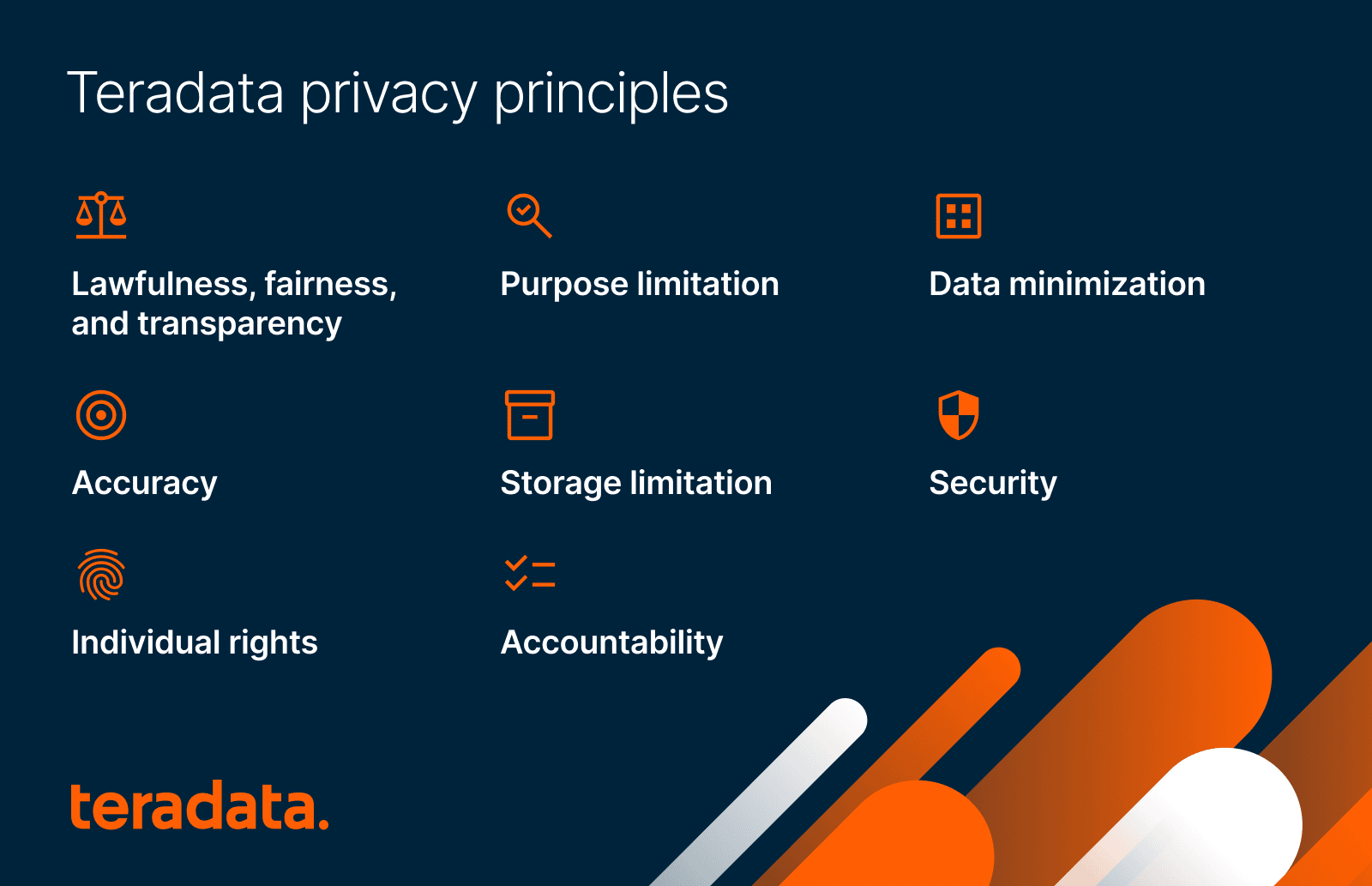
Transparency, accountability, and individual rights are some of the most important data privacy principles. As a best practice, many organizations incorporate these and other points into their own frameworks. Teradata recognizes and adheres to eight data privacy principles:
- Lawfulness, fairness, and transparency. Personal data should be used lawfully, fairly, and in a way that is transparent to the individual to whom it belongs.
- Purpose limitation. Personal data may only be collected for specific, legitimate purposes and may not be reused in a way that does not align with those purposes.
- Data minimization. The personal data collected or used must be limited to only the information necessary for achieving the specified, legitimate purposes for collecting the information.
- Accuracy. Personal data must be accurate and, where necessary, kept up to date.
- Storage limitation. Personal data should be kept only so long as necessary for the specified, approved uses or to meet the company’s legal obligations, after which it should be deleted or fully anonymized.
- Security. Personal data should be appropriately secured against unauthorized or unlawful access, loss, destruction, or damage. Confidentiality, integrity, and accessibility must be maintained.
- Individual rights. Individuals have the right to request access, make changes, or object to the use of their personal data.
- Accountability. Those who process personal data are responsible for demonstrating compliance with the privacy principles.
What are examples of data privacy?
Examples of data privacy include practices such as:
- Encrypting personal data to protect it from unauthorized access
- Enforcing strict access controls to ensure that only authorized personnel can access sensitive information
- Providing privacy notices that clearly explain how personal data is collected, used, and shared
- Obtaining explicit consent from individuals before processing their personal data
- Allowing individuals to opt out of data processing activities
- Conducting regular privacy impact assessments to identify and mitigate privacy risks
- Implementing privacy by design
These practices demonstrate an organization's commitment to protecting personal data and complying with data privacy regulations, fostering trust and confidence among consumers and stakeholders.
Secure your data. Build trust.
Modern business is deeply interconnected, creating both opportunities and risks. Teradata safeguards data with best-in-class technologies and processes, earning the trust of leading enterprises from the world’s most highly regulated industries. To learn more about how Teradata delivers trusted data for business, visit our Trust and Security Center.
This content is for information-only purposes. The content isn’t intended to constitute legal advice and shouldn’t be relied on as such. Organizations should consider the content based on their individual circumstances. Teradata recommends customers take their own independent professional advice on the matters contained in this document.